Hackers Took a Break: A Cybersecurity Pause on December 31st and Global Unity in Celebration. Threat Report: 25th-31st December 2023

Introduction
Foresiet's close monitoring of data breaches reveals a unique observation: On the 31st of December, there were no reported breaches. This hiatus in cyber threats suggests a universal celebration of New Year's, uniting even the diverse worlds of hackers and everyday individuals. Despite differences, the global community came together in a shared moment of celebration.
Alongside, the cybersecurity landscape witnessed significant shifts during the week of 25th to 31st December 2023, marked by a decline in emerging trends and pivotal changes in threat dynamics. This comprehensive report provides an overview of key observations, additional data points, the latest cybersecurity updates, and an in-depth analysis of vulnerabilities across various fronts.
Key Observations for the Week
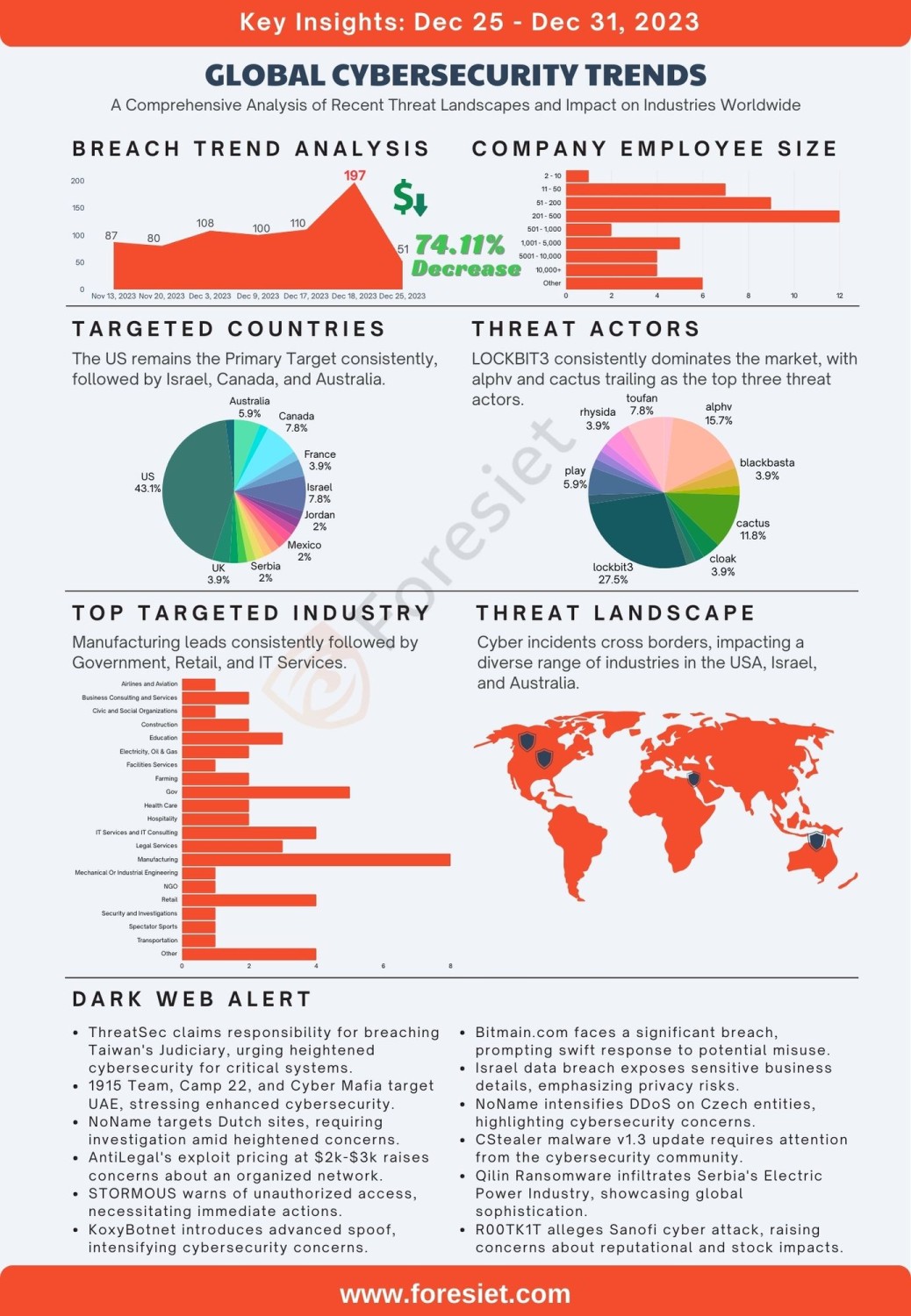
- Total Breaches: A notable decline in cyber breaches marked a 74% decrease from 197 breaches last week to 51 breaches this week, signifying a substantial shift in the overall threat landscape.
- Primary Targets: Companies with 201 to 500 employees emerged as primary targets, showcasing an increased focus on this specific size range. This trend underscores the adaptability of threat actors and the need for tailored cybersecurity measures for businesses within this demographic.
- Industries Facing Heightened Threats: Manufacturing remains the primary target, emphasizing the industry's vulnerability. Government organizations witnessed an unusual surge in breaches, surpassing incidents reported in the last two months. Additionally, retail and IT services experienced increased threats, highlighting the evolving nature of cyber risks across diverse industries.
The Rise of New Threat Actors
The cybersecurity landscape has witnessed a notable shift in threat actor group dominance over the past week. This week's analysis unveils a significant change in the hierarchy of threat actors, underscoring the adaptability and variability within the cyber threat landscape. Here's a comparison of the number of threats imposed by prominent groups:
- Lockbit3 Group: This week, the Lockbit3 group took the lead with 14 breaches, showcasing a notable increase in their activities. In comparison, last week, they accounted for 21 breaches, marking a slight decrease. Despite this, Lockbit3 remains a prominent threat actor.
- Toufan's Drastic Drop: The most striking observation lies in the drastic drop in breaches during the last week of December. Toufan, which held the top position mid week with a staggering 108 breaches, experienced a significant decrease. This week, their count dropped to 21 breaches, indicating a substantial decline in their cyber activities.
- Alphv's Consistent Presence: Alphv maintains a strong presence, securing the second position with 8 breaches this week, compared to 6 breaches last week. The consistent ranking in the top three threat actors indicates Alphv's sustained impact and underscores the need for vigilant monitoring of their activities.
The shift in the top threat actors, along with the continued presence of Alphv, Play, and Cactus, highlights the dynamic nature of the cybersecurity landscape. As we delve into these nuances, it becomes clear that threat actor activities can fluctuate significantly, emphasizing the importance of continuous monitoring and adaptation of cybersecurity measures.
Employee Size Vulnerabilities
Cyber threats exhibit a diverse impact across company sizes. Notably, businesses with 201 to 500 employees face heightened risks, with 12 reported breaches. Smaller enterprises, ranging from 11 to 50 employees, encountered 7 breaches, emphasizing their vulnerability.
Larger corporations with 1,001 to 5,000 employees reported 5 breaches, reinforcing the need for robust cybersecurity, while even the most extensive organizations with over 10,000 employees weren't immune, experiencing 4 breaches.
Attack Surface Exposure
- This week, we identified 438 vulnerabilities, with 50 classified as critical. Out of the overall 438 vulnerabilities, 18 already have available exploits, with 15 classified as critical vulnerabilities. Worth noting that these vulnerabilities carry an EPSS score ranging from 0.04% to 0,1%, indicating a High Level of Potential Exploitation.
- Foresiet research team has identified exploits available for Opportunistic Threat actors, to target easy attacks. Listing a few: CVE-2023-52181, CVE-2023-51505, CVE-2023-51475, CVE-2023-51473, CVE-2023-51468, CVE-2023-51419, CVE-2023-51411, etc.,
Recent Threats in the Dark Web Community
From a new strain of malware, Lust Stealer, to LockBit 3.0 ransomware targeting a British accountancy firm and emerging ransomware group WereWolves, this section outlines significant threats and breaches. Collaboration among ransomware groups and the Russian Cyber Army's strategic targeting add urgency to cybersecurity efforts.
- Taiwan Judiciary System Breach: ThreatSec infiltrates Taiwan's Judiciary System, compromising 500,000 lines of sensitive data, emphasizing the need for heightened cybersecurity.
- Indian Website Data Leak: Team Cyber Mafia and The Camp 22 leak data, urging urgent cybersecurity measures to address potential repercussions.
- Coordinated Attacks in UAE: Hacktivist groups 1915 Team, Camp 22, and The Cyber Mafia launch coordinated attacks on Abu Dhabi government entities, signaling an alarming escalation in cybersecurity threats.
- NoName's Cyber Attacks in the Netherlands: NoName orchestrates cyber-attacks on critical Dutch websites, posing a significant threat to the country's digital infrastructure, and requiring a thorough investigation.
- Crosslinking Exploit for Sale: AntiLegal advertises a sophisticated crosslinking exploit in the underground market, raising concerns about potential malicious activities and an organized trading network.
- STORMOUS Ransomware Warning: STORMOUS Ransomware warns about selling unauthorized access to internal networks, highlighting compromised credentials for Palo Alto Networks' VPN GlobalProtect.
- KoxyBotnet's Advanced Spoof: KoxyBotnet introduces a new spoof with advanced capabilities for Layer 4 and Layer 7 attacks, emphasizing potential cybersecurity vulnerabilities.
- Bitmain.com Data Breach: Bitmain.com faces a significant data breach impacting 300k global users in the cryptocurrency sector, raising concerns about potential misuse.
- Israel Data Breach: NoName intensifies cyber activities in Israel, exposing sensitive business details and Facebook data, and emphasizing widespread privacy risks.
- DDoS Attacks in the Czech Republic: NoName targets critical institutions in the Czech Republic with DDoS attacks, underscoring heightened cybersecurity concerns.
- CStealer Malware Update: CStealer malware introduces substantial enhancements in version 1.3 (2023-21-12), raising concerns about increased potency and versatility.
- Qilin Ransomware in Serbia: Qilin Ransomware Group infiltrates the Electric Power Industry of Serbia, highlighting the group's global reach and focus on critical infrastructure.
- Sanofi Cyber Threat: R00TK1T targets pharmaceutical giant Sanofi, alleging a successful cyber-attack and threatening to expose a purportedly exfiltrated database, raising concerns about potential reputational and stock impacts.
Key Considerations for Organizations
- Tailored Security Measures: Organizations should adopt tailored security measures based on their employee size, understanding that threat actors may exploit specific vulnerabilities associated with each category.
- Continuous Vigilance: A proactive and continuous vigilance approach is crucial. Regularly assess and update security protocols to adapt to emerging threats.
- Employee Training: Invest in comprehensive cybersecurity training for employees at all levels. Creating a cyber-aware culture is pivotal in preventing breaches.
- Collaboration and Information Sharing: Foster collaboration within industry sectors to share threat intelligence and best practices. Collective efforts strengthen the overall resilience against cyber threats.
- Technology Adoption: Leverage advanced cybersecurity technologies, such as AI-driven threat detection and response systems, to stay ahead of evolving threat tactics.
Conclusion
In a world of evolving cyber threats, staying informed is the first line of defense. Foresiet team provides you with timely and insightful updates to empower your cybersecurity strategies. As we conclude this week's report, remember to stay vigilant, adapt to changing landscapes, and collaborate to build a resilient defense against the ever-evolving cyber threats.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


March 12, 2024, 5:13 p.m.

Feb. 5, 2024, 5:13 p.m.