Navigating the Tides of Cybersecurity: Trends and Insights (8th - 14th Jan 2024)

Introduction
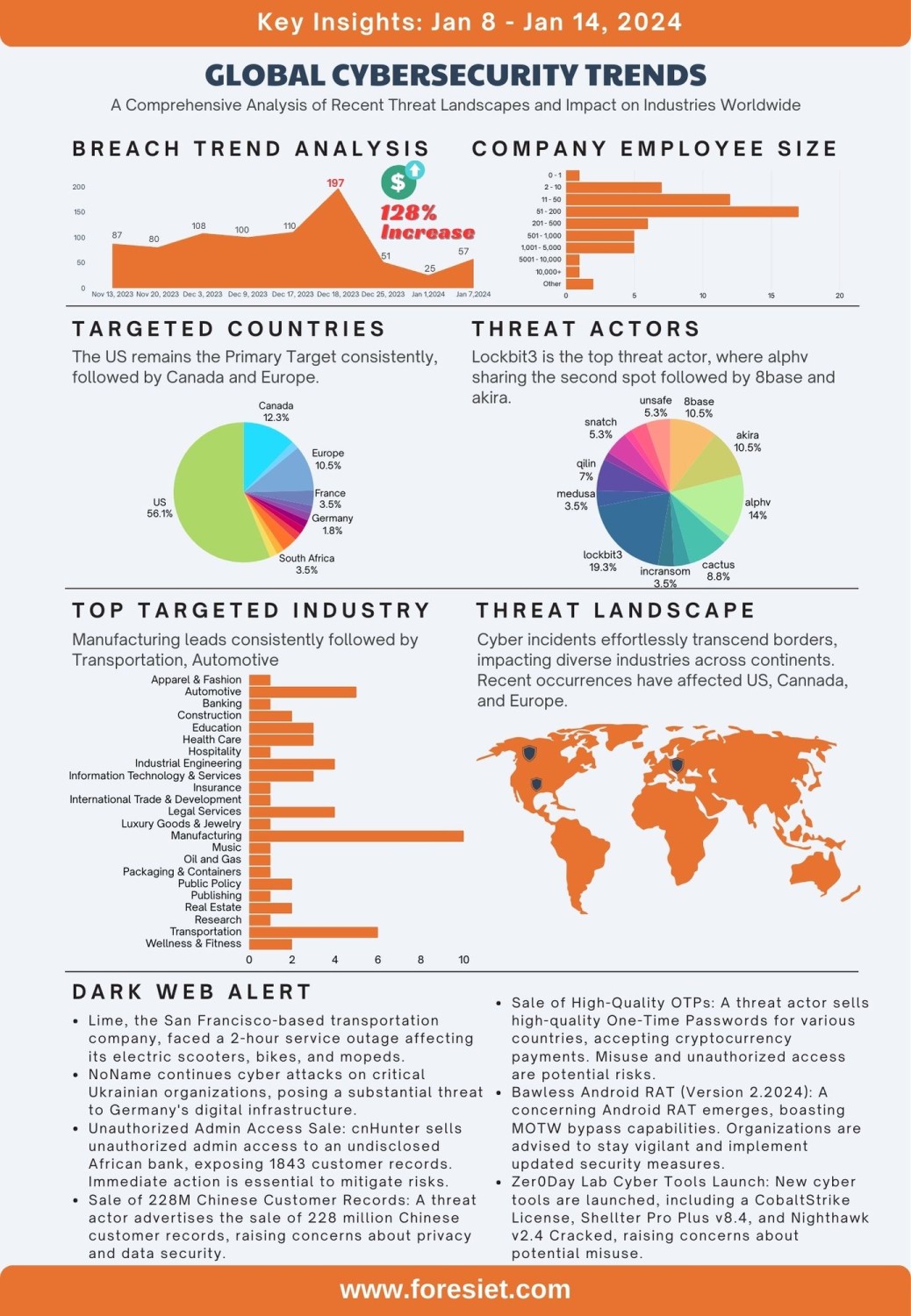
In the ever-evolving landscape of the digital realm, cybersecurity is experiencing rapid transformation. As we delve into the week spanning January 8th to January 14th, 2024, a panorama of dynamic shifts comes to light, characterized by a notable 128% surge in breaches. Significantly, the continuous presence of Lockbit3, a prominent threat actor group, commands attention over this period. This newsletter aims to provide a comprehensive overview, combining key observations, additional data points, the latest developments in cybersecurity, and a detailed analysis of vulnerabilities based on employee size. I invite you to join us as we navigate through the intricacies of this evolving cyber terrain, where each revelation underscores the imperative for heightened vigilance and fortified cybersecurity measures.
Cybersecurity Landscape Recap: A 128% Surge in Breaches
In the past week, the cybersecurity domain witnessed a substantial 128% increase in breaches, signaling a critical need for a thorough examination of the evolving threat landscape. Amidst this surge, Lockbit3 emerged as a prominent threat actor group, contributing significantly to the heightened breach activity. This dual revelation emphasizes the urgency for organizations to not only analyze the quantitative spike in breaches but also to discern the specific threat actors orchestrating these incidents, guiding a more strategic and targeted cybersecurity response.
Size Matters: Breach Patterns Across Company Scale
A detailed analysis of breaches based on company size revealed intriguing patterns. Entities with 51 to 200 employees reported the highest percentage of breaches, closely followed by businesses with 11 to 50 employees, smaller organizations with 2 to 10 employees, and larger companies with 201 to 500 employees. This nuanced breakdown underscores the necessity for tailored cybersecurity strategies based on company size.
Bullseye on Industries: Threats Intensify in Manufacturing and Beyond
The manufacturing sector maintained its unfortunate status as the most targeted industry, with the transportation and automotive sectors closely trailing behind. This concentrated focus highlights the urgent need for industry-specific cybersecurity approaches to mitigate threats effectively.
Unveiling the Top Threat Actors and Their Activities
This week's scrutiny of the threat actor landscape has provided valuable insights, revealing noteworthy contributors to the surge in cybersecurity breaches.
- Leading the Pack: Lockbit3's Impact with 11 Breaches Lockbit3 has emerged as a prominent threat actor, taking the lead with 11 reported breaches, significantly influencing the overall surge. Following closely are Alphv and Akira, with 8 and 6 breaches, respectively, collectively shaping a substantial portion of the current threat landscape.
- Diverse Contributors: Mid-Tier Threat Actors in the Mix Contributions from mid-tier threat actors, including Cactus, Qilin, Threeam, Everest, Incransom, Medusa, Snatch, and Unsafe, have been added to the incident pool with varying levels of activity. This diverse range of contributors underscores the nuanced nature of the evolving threat landscape.
- In-Depth Analysis of Lockbit3: 266.67% Increase in Breaches A closer examination of Lockbit3 reveals its consistent prominence, having posed 3 threats last week. However, a substantial escalation is evident, with 11 threats collectively reported this week. It is essential to clarify that this figure represents the combined impact of breaches, marking a 266.67% increase in Lockbit3's overall activity. This highlights the dynamic tactics and growing impact of threat actors, emphasizing the need for organizations to maintain heightened vigilance.
Employee Size Vulnerabilities
The threat landscape revealed a striking pattern in breach distribution across different company sizes. Companies with 51 to 200 employees experienced the highest breach count, followed by businesses with 11 to 50 employees and smaller entities with 2 to 10 employees. Larger organizations with 201 to 500 employees encountered the fourth-highest breach count, emphasizing the need for tailored cybersecurity measures.
Attack Surface Exposure
- This week brought to light a total of 881 vulnerabilities, with 133 deemed critical. Among these, 178 vulnerabilities have available exploits, with 113 falling under the critical category. Notably, these vulnerabilities carry an EPSS score ranging from 0.04% to 0.55%, signaling a High Level of Potential Exploitation.
- The research team at Foresiet pinpointed exploits tailored for Opportunistic Threat actors, focusing on easily exploitable vulnerabilities. Noteworthy examples include CVE-2024-0252, CVE-2023-52219, CVE-2023-52218, CVE-2023-7221, CVE-2023-7220, CVE-2023-52225, CVE-2024-21650, and more. This underscores the imperative for organizations to stay vigilant and address vulnerabilities promptly.
Recent Threats in the Dark Web Community
In the obscured realms of the dark web, a tapestry of cyber threats unfolds, encompassing disruptions to prominent urban transportation services, targeted cyber attacks on critical Ukrainian and German organizations, illicit transactions of unauthorized admin access, and vast troves of sensitive customer records, the sale of high-quality One-Time Passwords (OTPs), and the emergence of a formidable Android RAT known as Bawless. As we delve into these findings, we confront the stark reality of the ever-evolving threats that challenge data security, privacy, and the integrity of digital landscapes worldwide. Join us in exploring the dark corners of cyberspace, where each revelation underscores the imperative for heightened vigilance and fortified cybersecurity measures.
- Lime, the San Francisco-based transportation company, faced a 2-hour service outage, impacting its electric scooters, bikes, and mopeds.
- NoName continues its cyber attacks on critical Ukrainian organizations, including Euro-Reconstruction Ltd, Accordbank, Zaporizhzhya Titanium-Magnesium Plant, State Tax Service, Central Interregional Tax Administration, Western Interregional Tax Administration, and Main Directorate of the State Tax Service in Kyiv.
- NoName intensifies cyber attacks targeting multiple websites in Germany, including the City of Rostock, City of Bremen, Authorization of City of Bremen, City of Dortmund, Federal Central Tax Office, Munich Transport Company, Rhine-Main Transport Association, and Verkehrsverbund Großraum Nurnberg. These attacks pose a substantial threat to Germany's digital infrastructure, necessitating a comprehensive investigation into the motives behind targeting specific entities.
- Unauthorized Admin Access Sale: A threat actor, identified as cnHunter, is reportedly selling unauthorized admin access to an undisclosed African bank. The actor claims access to 1843 customer records, including names, account numbers, and phone numbers. This incident raises serious concerns about the security of customer data, emphasizing the need for immediate action to mitigate potential risks and enhance overall cybersecurity measures.
- Sale of 228M Chinese Customer Records: A threat actor is advertising the sale of 228 million Chinese customer records, comprising sensitive information such as names, phone numbers, social codes, company details, industries, financial data, addresses, and cities. The sale, which includes a vast amount of personal data, poses a significant risk to individuals' privacy and highlights the ongoing challenges in safeguarding sensitive information.
- Sale of High-Quality OTPs: A threat actor is advertising the sale of high-quality One-Time Passwords (OTPs) for various countries, including Russia, Malaysia, the United States, and Indonesia. These OTPs can be utilized for applications such as KFC, Netflix, DisneyHotstar, McDonald's, Burger King, Binance, Twitter, ProtonMail, and more. The actor accepts payments in XMR (Monero), LTC (Litecoin), and BTC (Bitcoin), with prices starting from $0.5. Bulk purchases are available at discounted rates, raising concerns about potential misuse and unauthorized access.
- The emergence of Bawless Android RAT (Remote Access Trojan), specifically in its Version 2.2024, presents a noteworthy threat in the recent cyber landscape. This Android-targeting remote control tool boasts the ability to install directly on devices without requesting permissions, leveraging Mark of the Web (MOTW) bypass techniques. Priced at $2300, it accepts payments in popular cryptocurrencies such as BTC, ETH, LTC, and USDT, offering a full version along with the source code. Each client reportedly receives a unique stub, enhancing the longevity of payloads. The associated Telegram channels provide updates, support, and insights into the Android RAT's usage, while the GitHub repository offers further technical details. Also, potential connections to Luxury Crypter raise concerns, so it's necessary to have additional analysis. Organizations and users are advised to remain vigilant, implement updated security measures, and avoid engaging with potential threats associated with Bawless Android RAT.
- Zer0Day Lab has recently launched new cyber tools, including a CobaltStrike License for 3 users with web access priced at £500 GBP, Shellter Pro Plus v8.4 (x86 & x64) also priced at £500 GBP, and Nighthawk v2.4 Cracked available for £250 GBP. For further information or inquiries, individuals can contact the provided channel @zerosuppbot. This development raises concerns about the potential misuse of these tools in cyber threats and underscores the ongoing challenges in cybersecurity.
Conclusion
In navigating the tides of cybersecurity, understanding these trends and insights is paramount. Organizations are urged to tailor their cybersecurity measures, staying proactive and adaptive in the face of evolving threats. As the digital landscape continues to evolve, a resilient cybersecurity strategy is the key to safeguarding against the ever-changing threat landscape.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


March 12, 2024, 5:13 p.m.

Feb. 5, 2024, 5:13 p.m.