Navigating the Tides of Cybersecurity: Trends and Insights (15th - 21st Jan 2024)

Introduction
In an era dominated by digital connectivity, where the exchange of information is constant and seamless, the pervasive threat of cyber incidents has become a formidable challenge for individuals, businesses, and nations alike. The past week has seen a significant surge in cyber breaches, with the impact felt across diverse industries and geographical boundaries. As we delve into the recent data, a compelling narrative emerges, weaving together elements of threat intelligence, the insidious rise of ransomware, and the crucial role of attack surface management. This narrative highlights the primary targets, exposes the prominent threat actors, and sheds light on the industries most affected by these evolving cybersecurity challenges.
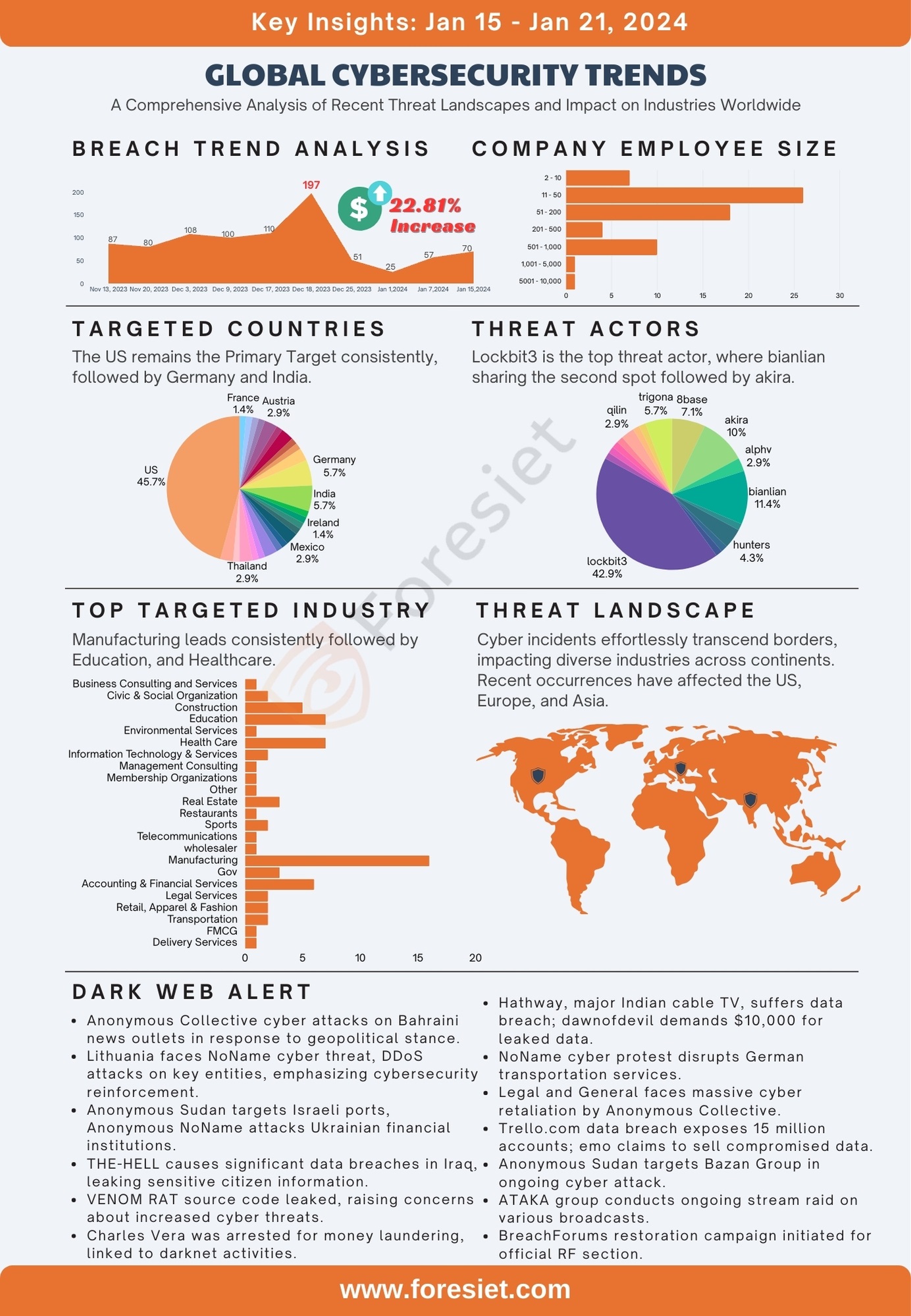
Recent Surge in India and a 22.81% increase in breaches globally
In a disconcerting development, recent data reveals a 22.81% increase in cyber breaches globally over the past week. This surge contributes significantly to the global spike in cyber incidents, raising concerns about the cybersecurity posture of nations and businesses alike. Whereas, India tends to be in the top targeted list this week. The need for heightened awareness, proactive measures, and international cooperation becomes ever more apparent in the face of evolving challenges in threat intelligence, the growing threat of ransomware, and the imperative role of attack surface management.
Global Targets
In the dynamic realm of cyber threats, certain patterns persist, and the United States stands resiliently as the primary target. Notably, recent data underscores a noteworthy shift, with Germany and India closely following suit. The three nations collectively bear the brunt of cyber adversaries seeking vulnerabilities and exploits, necessitating a robust focus on threat intelligence, vigilant defense against the growing threat of ransomware, and strategic attack surface management.
Among the threat actors, Lockbit3 emerges as the top contender, showcasing a sophisticated and persistent modus operandi. Sharing the second spot are Bianlian and Akira, further intensifying the landscape of cybersecurity challenges. These actors employ diverse tactics, from ransomware to social engineering, creating a multifaceted threat landscape that demands continuous vigilance.
Industry Dynamics
Manufacturing consistently takes the lead, facing relentless attacks, followed closely by the Education and Healthcare sectors. These attacks not only compromise sensitive information but also disrupt critical services, underscoring the need for robust cybersecurity measures across diverse sectors. Implementing effective threat intelligence, fortifying defenses against the persistent threat of ransomware, and strategically managing the attack surface are imperative for safeguarding these sectors.
Global Impact: Cyber Incidents Know No Borders
Cyber incidents effortlessly transcend geographical borders, leaving a trail of disruption in their wake. Recent occurrences have affected not only the United States but also Europe and Asia, emphasizing the global nature of cyber threats. The integration of effective threat intelligence, proactive measures against ransomware, and strategic attack surface management is vital in enhancing our global cybersecurity posture.
Employee Size Matters: Breaches by the Numbers
An analysis of breach incidents based on employee size sheds light on the varying degrees of vulnerability. Organizations with an employee size of 11-50 faced 26 breaches, underscoring the challenges small to medium-sized enterprises encounter. Those with 51-200 employees experienced 18 breaches, while organizations with 501-1,000 employees faced 10 breaches. This nuanced understanding of breach distribution can inform tailored cybersecurity strategies based on organizational size. Implementing effective threat intelligence, robust measures against ransomware, and strategic attack surface management is crucial to addressing vulnerabilities across diverse organizational sizes.
Analysis of Current Attack Surface Exposure
This week, our analysis revealed a total of 600 vulnerabilities, with 53 categorized as critical. Notably, 73 of these vulnerabilities already possess available exploits, with 9 falling under the critical classification. It's essential to highlight that these vulnerabilities carry an EPSS score ranging from 0.04% to 10.26%, signifying a High Level of Potential Exploitation.
The Foresiet research team has specifically identified exploits tailored for Opportunistic Threat actors, focusing on easy targets. Some notable vulnerabilities include CVE-2023-6049, CVE-2023-5905, CVE-2023-3211, CVE-2023-0224, CVE-2022-1609, CVE-2020-36770, CVE-2011-10005, and more. This observation underscores the need for vigilant cybersecurity measures to address the existing vulnerabilities and potential threats associated with the identified exploits.
Unveiling the Top Threat Actors and Their Activities
In a comprehensive examination of the threat actor landscape based on the provided data, certain groups have emerged as particularly noteworthy. The following threat actor groups, along with their counts and percentages, shed light on the prominence and potential impact of each in the cybersecurity domain:
- Lockbit3: Standing out with the highest count of 30, this group constitutes 42.86% of the total occurrences.
- Bianlian: Holding the second spot, Bianlian has a count of 8, representing 11.43% of the total occurrences.
- Akira: Following closely with a count of 7, Akira makes up 10% of the total occurrences.
- 8base: Although not in the top 3, 8base still boasts a substantial count of 5, accounting for 7.14% of the total occurrences.
- Trigona: Rounding up the top 5 threat actor groups with a count of 4, Trigona constitutes 5.71% of the total occurrences.
This analysis underscores the significance of monitoring these groups closely given their frequency and potential impact on cybersecurity.
Dark Web Threats
The dark web landscape is rife with cyber threats and geopolitical implications, evident in recent incidents targeting Bahraini news outlets and Lithuania. NoName, an elusive threat group, claims responsibility for DDoS attacks in Lithuania, adding complexity with potential geopolitical motives. Anonymous Sudan and NoName further escalate tensions, launching cyber attacks on Israeli ports and Ukrainian financial institutions. The-Hell's significant data breach in Iraq exposes sensitive information, raising concerns about privacy and identity theft. Additionally, the leaked source code for the VENOM Remote Access Trojan poses an increased risk, emphasizing the evolving and multifaceted challenges in the dark web environment.
- In response to Bahrain's support for the US initiative against Houthi rebels in the Yemeni conflict, the Anonymous Collective has initiated cyber attacks targeting prominent Bahraini news outlets. The affected organizations include Akhbar al-Khaleej, Al-Ayam, Gulf News Daily, and Al-Bilad. This cyber offensive is emblematic of a digital protest against Bahrain's geopolitical stance, and the situation is actively being monitored to assess its impact on the region and potential repercussions in cyberspace. The collective's actions underscore the growing intersection of cyber activities and international relations, prompting concerns about the broader implications on digital security. Key hashtags such as #Cyberattack, #Bahrain, #DDoS, #YemenConflict, #USA, #MiddleEastConflict, and #MiddleEast are emerging in discussions surrounding this incident. As the situation unfolds, there will likely be increased scrutiny on the evolving dynamics between cyber activities and geopolitical developments in the Middle East.
- In a concerning development, Lithuania, recognized for its substantial support to Ukraine relative to its GDP, is now grappling with a significant cyber threat. The elusive threat group known as NoName has recently claimed responsibility for a series of Distributed Denial of Service (DDoS) attacks targeting key Lithuanian entities. The entities affected include Compensa Insurance Company, If Insurance Company, Lithuanian Roads, a logistics company, Internet Provider Init, and Internet Provider Balticum (Closed - Geo Restriction).
- NoName's assertion of responsibility adds a layer of complexity to the situation, hinting at a potential motive linked to ongoing geopolitical events. As a precautionary measure, organizations in the region are being advised to fortify their cybersecurity measures to effectively counter and mitigate potential risks posed by these cyber attacks.
- The specific targets and URLs affected by the DDoS attacks include Compensa Insurance Company, If Insurance Company, Lithuanian Roads, the logistics company, Internet Provider Init, and Internet Provider Balticum (Closed - Geo Restriction). These organizations are encouraged to conduct thorough checks on their website performance and response, utilizing online monitoring tools to ensure the integrity and availability of their online platforms.
- The threat group, NoName, is identified by its utilization of DDoS attacks as its preferred method, and their acknowledgment of responsibility raises concerns about the potential geopolitical motivations behind these cyber assaults. This incident serves as a stark reminder of the susceptibility of nations to cyber threats, especially against the backdrop of evolving geopolitical dynamics.
- In response to the emerging cyber threat, the incident has garnered attention on social media platforms with hashtags such as #Lithuania, #CyberSecurity, #DDoSAttack, #ThreatIntel, and #NoNameGroup being widely used. As the situation continues to unfold, it is imperative for entities in the region to remain vigilant, enhance their cybersecurity posture, and actively monitor developments to safeguard against potential repercussions stemming from these cyber attacks. Stay tuned for further updates on this evolving situation.
- Anonymous Sudan has claimed responsibility for a significant cyber attack on Israeli ports, targeting vital infrastructure including ISRAEL PORTS DEVELOPMENT and Haifa Port Company Ltd. The attack aimed at disrupting network devices, administration systems, servers, and endpoints, impacting the digital health of these crucial entities. The threat actor has also hinted at future targets, notably Israel's Credit Card Company CAL. Key hashtags circulating include #CyberAttack, #IsraelPorts, #AnonymousSudan, and #ThreatIntel, underlining the severity of the situation. Stay tuned for updates on this evolving cyber threat.
- NoName has claimed responsibility for cyber attacks on Ukrainian financial institutions, including Acordbank, Credit Agricole Bank, and Pravex Bank. The hacktivist group executed Distributed Denial of Service (DDoS) attacks, disrupting online services and posing potential operational challenges for the targeted banks. The threat actor, NoName, is known for its hacktivist engagements. Key hashtags circulating include #CyberAttack, #NoName, #Ukraine, #FinancialInstitutions, #DDoS, and #ThreatIntel, indicating the severity of the situation. Stay tuned for updates on the evolving response to these cyber threats.
- A significant data breach affecting Iraqi citizens has been attributed to the threat actor known as THE-HELL. The breach, reported on Monday, January 8, 2024, at 02:11 PM (UTC), exposed sensitive information, including full names, names of family members, year of birth, exact residential addresses, and various personal details. The leaked database encompasses all governorates in Iraq, raising concerns about privacy and potential identity theft. Key hashtags circulating include #DataBreach, #Iraq, #Privacy, #ThreatIntel, #IdentityTheft, and #Cybersecurity. Stay vigilant for updates on this developing incident.
- The cybersecurity landscape faces a notable threat as the original source code for the VENOM Remote Access Trojan (RAT) has been leaked by an actor identified as empme. This significant incident, occurring on Friday, September 1, 2023, at 02:59 PM (UTC), raises concerns about potential exploitation of vulnerabilities and unauthorized activities. VENOM RAT, renowned for providing unauthorized remote access to compromised systems, now poses an increased risk as threat actors can customize and deploy their versions of the malware. Stay informed and vigilant for developments on this critical cybersecurity issue.
- Charles Vera, also known as "Weep," has been apprehended on charges of money laundering following an investigation by the Bergen County Prosecutor's Office and the Dumont Police Department. The arrest, which took place on June 28, 2023, at 546 Washington Avenue, Apt. 3206, Dumont, NJ, stems from Vera's alleged involvement in darknet activities, including brokering transactions on darknet marketplaces. The charges against him include second-degree financial facilitation of criminal activity (money laundering)
Conclusion:
In the ever-evolving landscape of cybersecurity, vigilance is paramount. The recent surge in cyber incidents, coupled with the dynamic nature of threat actors and the global impact on industries, demands a collective and proactive response. As we confront these challenges, collaboration, innovation, and a commitment to robust cybersecurity practices, including strategic measures for threat intelligence, defense against ransomware, and efficient attack surface management, will be essential in safeguarding our digital future. The interconnected world calls for united efforts to fortify our defenses and mitigate the ever-present risks in cyberspace.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


March 12, 2024, 5:13 p.m.

Feb. 5, 2024, 5:13 p.m.